Overview
Along with the digitalization in the contemporary world, everybody’s concern about the privacy of their personal information is also enhancing day by day. To elaborate, employers are concerned about threats like theft of intellectual property, and breach of sensitive data , whereas, employees feel insecure about the fact that every single activity is monitored by their employers. Furthermore, consumers too are concerned about the breach of their privacy in terms of their personal information going public or being accessed by multiple parties. Hence, all the concerned stakeholders are trying their best to minimize the possibility of such occurrences.

Probing further, technology has a major role in laying the foundation for these concerns in the business world. Because technology has made it easier for data exploiters or hackers to peep into the private information that can cause harm to the company or consumers. The easier access and increased chances of exploitation of sensitive information made a Invasion of privacy an ethical issue in the business world. The Invasion of privacy occurs usually for monetary benefits and statistics also validate that 71% of the breaches are financially motivated. Further, the privacy of breach can be comprehended in 3 different contexts.
Table of Contents
In the context of employers
Further elaborating, in regards to employers’ concerns, monitoring the employees’ activities came out as the best possible solution for many employers. Surveilling their activities assisted them in keeping an eye on the employees that could assist in identifying the potential threats to the company. Theft of sensitive data or intellectual property using various applications and selling nonpublic information in exchange for monetary or other benefits can be some of how employees can compromise the privacy of the company. This can negatively impact the growth and cause a hindrance in the successful accomplishment of the SMART goals of the company. To reduce these risks, employers should ensure that confidential information is only shared with employees on a need-to-know basis. For instance, when a new employee joins the company, performing a factory reset on any company-issued device, such as a MacBook, can help ensure that no personal information from a previous employee is inadvertently transferred.
In the context of employees
As important, as it became for employers to keep a check on employees' activities, on the same hand, employees also expected respect for their privacy. However, some employers didn't realize the difference between breaching privacy and surveilling the activities of employees. This lack of realization leads to the increasing frustration of employees further increasing employees’ job dissatisfaction. Disclosing private information, and tracking employees in non-work-related spaces are some of the aspects where employees’ privacy can be invaded by employers.
In the context of consumers
Flipping to the other side of the coin, with consumers becoming more and more aware of the cases of data breaches in the enterprise world, their concerns about their privacy are also enhanced. As appealing as the trend of hyper-personalization to attract consumers is, employers also need to respect the privacy of their consumers. The utilization of illegal apps and software to track every minute detail of the consumers without their consent can lead to the invasion of privacy of consumers.
Measures to avoid privacy invasion
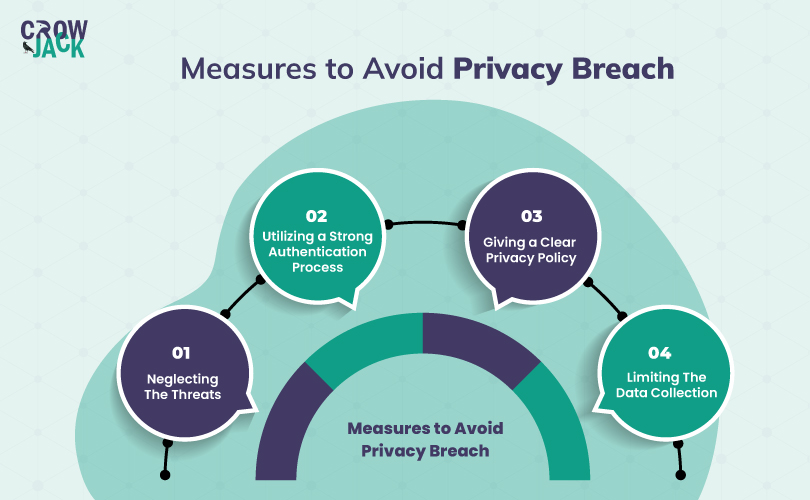
Moving ahead, multiple methods are listed below that can be adopted by the businesses to eliminate the threats along with perpetuating the privacy of consumers and employees -
1. Neglecting the threats
Major reason that hackers are able to get access to the personal data of the company is that employers often fail to notice the potential threats. Hence, it is crucial for employers to understand and identify the potential threats in the company and mitigate the risk of breaching private information.
2. Utilizing a strong authentication process
Employers need to encrypt the collected data with a strong authentication process. So that no hackers can break into sensitive data using any illegal technology. Enabling two-factor authentication can be an effective method of implementing a strong authentication to the systems with sensitive data.
3. Giving a clear privacy policy
To respect the privacy of consumers, it is important to provide all the details of usage of data in the privacy policy of the organization legally to make your consumers feel secure with sharing data with a company.
4. Limiting the data collection
Remember every time a business collects any sort of data from consumers, they become liable for storing that information with security. Therefore, employers should always focus on collecting limited and essential information that can help them for business growth.
To thoroughly understand, a detailed case study of Yahoo is presented, in which due to an employee and company’s carelessness, the company has to pay a huge amount. Let’s get into the case study without any ado
Real-life case study
Consumer’s privacy breach by Yahoo
We all know Yahoo as one of the prominent web service providers that are popular all across the world. However, a case of privacy breach of consumers by Yahoo came out in 2016 when a former employee of Yahoo, Reyes Daniel Ruiz admitted that he invaded the privacy of more than 6000 accounts while working for the company. He hacked those accounts and then used the information to access DropBox, iCloud, and Facebook in order to search for personal pictures and videos of young women.
As per the U.S Attorney's office of California, When the company got to know about this act, they destroyed the hard drive and computers he used to store the stolen information. Even in 2013, hackers managed to steal the data belonging to almost 3 billion users and the company did not acknowledge the issue until 2016. As a consequence, Yahoo lost almost 500 million international users by 2016.
When proven guilty, Ruiz got sentenced to 5 years in prison. This act impacted the company negatively for a long time. In fact, the company's British subsidiary had to pay a fine of £250,000 by the UK's Data Watchdog in 2018.
Key takeaway- One single unethical act from the employee’s side and not actively responding to the issue of a data breach, the company had to pay a huge amount in the terms of reputation loss, in monetary terms and the company also lost a large number of users. Hence, it is really crucial for employers to avoid such issues and even if something happens, strict and immediate action should be taken by the company to promote zero tolerance for such unethical acts in the cultural dimensions of the company.
FAQs
What should I do if I think my privacy has been violated at the workplace?
It's critical to act quickly and take immediate steps to deal with the problem if you suspect a privacy violation. Inform the IT and security personnel at your company, and, if necessary, get advice from legal and regulatory professionals to determine the extent of the incident and adhere to any applicable data breach reporting laws. Prompt action can show a commitment to protecting people's privacy and assist prevent any harm.
What function do privacy laws serve in dealing with privacy violations?
Organizations are required by law to uphold the rights of individuals to their data privacy under the General Data Protection Regulation (GDPR) in the European Union and the California Consumer Privacy Act (CCPA) in the United States. These regulations frequently mandate that businesses establish security controls, notify customers of security breaches, and maintain open data processing procedures.
Previous Issue
Unethical Accounting PracticesNext Issue
Environmental Responsibility
 Proof Reading
Proof Reading  Copy Writing
Copy Writing  Resume Writing
Resume Writing  Blogs
Blogs Guides
Guides SOP's
SOP's Student Resources
Student Resources Research Topics
Research Topics Login
Login Register
Register